Helm Chart Deployment steps for Workload Security Usecase
A collection of helm charts for Workload Security Usecase
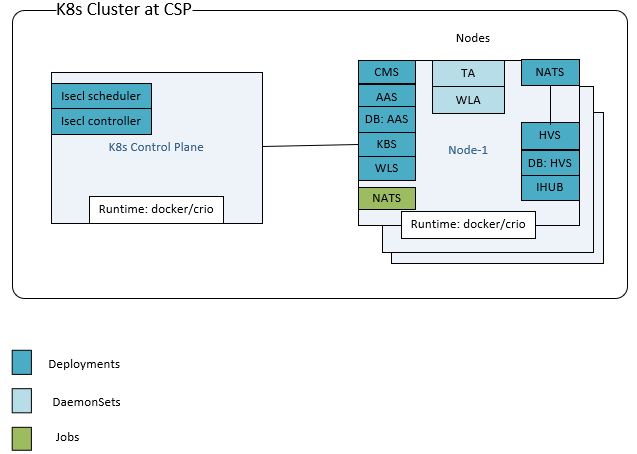
Deployment diagram
Getting Started
Below steps guide in the process for installing isecl-helm charts on a kubernetes cluster.
Pre-requisites
- Non Managed Kubernetes Cluster up and running
- Helm 3 installed
curl -fsSL -o get_helm.sh https://raw.githubusercontent.com/helm/helm/master/scripts/get-helm-3 chmod 700 get_helm.sh ./get_helm.sh -
For building container images Refer here for instructions
- Setup NFS, Refer instructions for setting up and configuring NFS Server
Support Details
| Kubernetes | Details |
|---|---|
| Cluster OS | RedHat Enterprise Linux 8.x Ubuntu 20.04 |
| Distributions | Any non-managed K8s cluster |
| Versions | v1.23 |
| Storage | NFS |
| Container Runtime | CRI-O |
Use Case Helm Charts
| Use case | Helm Charts |
|---|---|
| Workload Security | cms aas hvs nats ta isecl-controller ihub isecl-scheduler kbs wls wla |
Setting up for Helm deployment
Create a namespace or use the namespace used for helm deployment.
kubectl create ns isecl
Create Secrets for ISecL Scheduler TLS Key-pair
ISecl Scheduler runs as https service, therefore it needs TLS Keypair and tls certificate needs to be signed by K8s CA, inorder to have secure communication between K8s base scheduler and ISecl K8s Scheduler.
The creation of TLS keypair is a manual step, which has to be done prior deploying the helm for Trusted Workload Placement usecase.
Following are the steps involved in creating tls cert signed by K8s CA.
```shell script
mkdir -p /tmp/k8s-certs/tls-certs && cd /tmp/k8s-certs/tls-certs
openssl req -new -days 365 -newkey rsa:4096 -addext “subjectAltName = DNS:
cat «EOF | kubectl apply -f - apiVersion: certificates.k8s.io/v1 kind: CertificateSigningRequest metadata: name: isecl-scheduler.isecl spec: request: $(cat server.csr | base64 | tr -d ‘\n’) signerName: kubernetes.io/kube-apiserver-client usages:
- client auth EOF
kubectl certificate approve isecl-scheduler.isecl
kubectl get csr isecl-scheduler.isecl -o jsonpath=’{.status.certificate}’
| base64 –decode > server.crt
kubectl create secret tls isecl-scheduler-certs –cert=/tmp/k8s-certs/tls-certs/server.crt –key=/tmp/k8s-certs/tls-certs/server.key -n isecl
*Note*: CSR needs to be deleted if we want to regenerate isecl-scheduler-certs secret with command `kubectl delete csr isecl-scheduler.isecl`
##### Create Secrets for Admission controller TLS Key-pair
Create admission-controller-certs secrets for admission controller deployment
```shell script
mkdir -p /tmp/adm-certs/tls-certs && cd /tmp/adm-certs/tls-certs
openssl req -new -days 365 -newkey rsa:4096 -addext "subjectAltName = DNS:admission-controller.isecl.svc" -nodes -text -out server.csr -keyout server.key -sha384 -subj "/CN=system:node:<nodename>;/O=system:nodes"
cat <<EOF | kubectl apply -f -
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: admission-controller.isecl
spec:
groups:
- system:authenticated
request: $(cat server.csr | base64 | tr -d '\n')
signerName: kubernetes.io/kubelet-serving
usages:
- digital signature
- key encipherment
- server auth
EOF
kubectl certificate approve admission-controller.isecl
kubectl get csr admission-controller.isecl -o jsonpath='{.status.certificate}' \
| base64 --decode > server.crt
kubectl create secret tls admission-controller-certs --cert=/tmp/adm-certs/tls-certs/server.crt --key=/tmp/adm-certs/tls-certs/server.key -n isecl
Generate CA Bundle ```shell script kubectl config view –raw –minify –flatten -o jsonpath=’{.clusters[].cluster.certificate-authority-data}’
Add the output base64 encoded string to value in caBundle sub field of admission-controller in usecase/trusted-workload-placement/values.yml in case of usecase deployment chart.
*Note*: CSR needs to be deleted if we want to regenerate admission-controller-certs secret with command `kubectl delete csr admission-controller.isecl`
##### Create Secrets for KBS KMIP Certificates
Copy KMIP Client Certificate, Client Key and Root Certificate from KMIP Server to Node where KMIP secrets needs to be generated.
```shell script
kubectl create secret generic kbs-kmip-certs -n isecl --from-file=client_certificate.pem=<KMIP Client Certificate Path> --from-file=client_key.pem=<KMIP Client Key Path> --from-file=root_certificate.pem=<KMIP Root Certificate Path>
Installing isecl-helm charts
-
Add the chart repository
shell script helm repo add isecl-helm https://intel-secl.github.io/helm-charts helm repo update -
To find list of available charts
shell script helm search repo --versions
Usecase based chart deployment (using umbrella charts)
Update values.yaml for Use Case chart deployments
Some assumptions before updating the values.yaml are as follows:
- The images are built on the build machine and images are pushed to a registry tagged with
release_version(e.g:v5.1.0) as version for each image - The NFS server setup is done either using sample script instructions or by the user itself
- The K8s non-managed cluster is up and running
- Helm 3 is installed
The helm chart support Nodeports for services to support ingress model, enable the ingress by setting the value ingress enabled to true in values.yaml file.
Update the hvsUrl, cmsUrl and aasUrl under global section according to the conifgured model.
e.g For ingress. hvsUrl: https://hvs.isecl.com/hvs/v2
For Nodeport, hvsUrl: https://<controlplane-hosntam/IP>:30443/hvs/v2
Use Case charts Deployment
```shell script
export VERSION=5.1.0
helm pull isecl-helm/Workload-Security –version $VERSION && tar -xzf Workload-Security-$VERSION.tgz Workload-Security/values.yaml
helm install
> **Note:** If using a separate .kubeconfig file, ensure to provide the path using `--kubeconfig <.kubeconfig path>`
## Setup task workflow.
* Refer [instructions](/helm-charts/docs/setup-task-workflow.html) for running service specific setup tasks
To uninstall a chart
```shell script
helm uninstall <release-name> -n <namespace>
To list all the helm chart deployments
shell script
helm list -A
Cleanup steps that needs to be done for a fresh deployment
- Uninstall all the chart deployments
- Cleanup the data at NFS mount and cleanup mounted data for trustagent under /etc/trustagent and /var/log/trustagent in all worker nodes where ta is deployed.
- Remove all objects(secrets, rbac, clusterrole, service account) related namespace related to deployment
kubectl delete ns <namespace>.
Note:
Before redeploying any of the chart please check the pv and pvc of corresponding deployments are removed. Suppose
if you want to redeploy aas, make sure that aas-logs-pv, aas-logs-pvc, aas-config-pv, aas-config-pvc, aas-db-pv, aas-db-pvc, aas-base-pvc are removed successfully.
Command: ```kubectl get pvc -n <namespace>``` && ```kubectl get pv -n <namespace>```