Secure Key Caching
Definitions, Acronyms, and Abbreviation
-
SKC -- Secure Key Caching
-
HSM -- Hardware Security Module
-
KBS -- Key Broker Service
-
SWK -- Symmetric Wrapping Key
Key Broker Service
The Key Broker Service (KBS) is typically deployed in the tenant environment, not the Cloud Service Provider (CSP) environment. KBS is effectively a policy compliance engine. Its job is to manage key transfer requests from SKC Clients, releasing keys only to those that meet policy requirements. A user admin can create and register keys in KBS. He can also create key policies and assign them to keys. A key policy specifies the conditions that the SKC Client must fulfill for keys that have the policy assigned to them to be released. Most of the information about an SKC Client is contained in the SGX quote that it sends to KBS. The SGX quote also contains a hash of the enclave's public key. KBS gets the public key along the quote so the hash in the quote allows to verify that the public key is genuine. If the SGX quote verification (attestation) is successful, KBS generates a Symmetric Wrapping Key (SWK), wraps it with the enclave public key and provisions it into the enclave, which can unwrap it since it has the corresponding private key. Application can then be provisioned into the SGX enclave after being wrapped with the SWK. Application keys are therefore never exposed to any software outside of the enclave.
KBS is shared with other Intel® SecL-DC components.
The Workload SGX Dependencies
This is a set of dependencies needed by SGX workloads.
The SKC Client
The SKC Client refers to a suite of libraries that applications that require key protection must link with. It's comprised of the SKC Library, which is an Intel® SecL-DC component and the Intel Crypto Toolkit. the SKC Client uses the workload SGX dependencies component. The SKC Library supports the PKCS#11 interface and is therefore considered as a PKCS#11 module from the host application perspective. The SKC Library uses Intel Crypto Toolkit to protect keys in an SGX enclave. When a key is requested by the host application, the SKC Library sends a request to the Key Broker Service (KBS) along with an SGX quote that is generated by the Crypto Toolkit. KBS releases the key after verifying the quote and evaluating the attributes contained in the quote. The key policy can also specify conditions that can't be verified with the SGX quote alone.
The SKC Client is typically deployed inside a tenant VM or container. It can also be used on bare metal. In all these deployments, the underlying platform is typically owned by a Cloud Service Provider (CSP) and is considered untrusted.
Architecture Overview
Note
SGX Attestation Infrastructure components need to be deployed in order to realize the SKC use case.
As indicated in the Features section, SKC provides 3 features essentially:
- SGX Attestation Support: this is the feature that CSPs provide to tenants who need to run SGX workloads that require attestation.
-
SGX Support in Orchestrators: this feature allows to discover SGX support in physical servers and related information:
-
SGX supported.
-
SGX enabled.
-
Size of RAM reserved for SGX. It's called Enclave Page Cache (EPC).
-
Flexible Launch Control enabled.
- Key Protection: this is the feature used by tenants using a CSP to run workloads with key protection requirements.
-
The high-level architectures of these features are presented in the next sub-sections.
Key Protection
Key Protection leverages the SGX Attestation support and optionally, the SGX support in orchestrators.
Key Protection is implemented by the SKC Client -- a set of libraries - which must be linked with a tenant workload, like Nginx, deployed in a CSP environment and the Key Broker Service (KBS) deployed in the tenant's enterprise environment. The SKC Client retrieves the keys needed by the workload from KBS after proving that the key can be protected in an SGX enclave as shown in the diagram below.
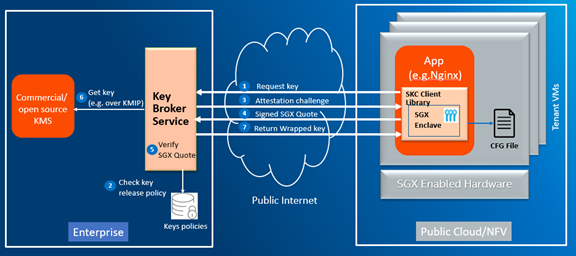
Step 6 is optional (keys can be stored in KBS). Keys policies in step 2 are called Key Transfer Policies and are created by an Admin and assigned to Application keys.
SKC Virtualization (Supported only on RHEL 8.2, not supported on Ubuntu 18.04/20.04)
Virtualization enabled on SGX Host machines, uses SGX key features. With Virtualization being enabled on SGX host, SKC Library which uses Intel crypto tool kit to protect keys in SGX Enclave can be configured on Virtual Machines which are created on SGX Hosts. This enhancement further provides the privilege for a workload on a VM allowing successful Secure Key transfer flow which meets the policy requirements. Hence virtualization on SGX Hosts supports key transfer flow for Workload on bare metal, Workload inside a VM, Workload in a container and Workload in a container inside a VM enabled on SGX Host.